Differential Power Analysis DPA is a powerful method for breaking the cryptographic system. Toolbox for advanced differential power analysis of symmetric key cryptographic algorithm implementations.

Introduction To Side Channel Power Analysis Sca Dpa Youtube
Large amount of traces Two main types of DPA.

. This tutorial will offer a brief but direct outline of how to use NONMEM with population analysis examples explaining all the instruction records and data file setups. During the session you will learn how to process the power trace. Therefore even systems using modern strong ciphers like AES are vulnerable to such attacks if proper countermeasures are not applied.
About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy Safety How YouTube works Test new features Press Copyright Contact us Creators. Ikizhvatov pysca. A analysis uses p o w er consumption measuremen ts to determine whether a k ey blo c kguess K s is correct.
Use hamming weight to guess power consumption of the least significant byte of the address. Support six fully differential inputs or twelv e single-ended inputs The content of this tutorial is not Differential casing thermal analysis We choose a 4 core machine for the computation to have enough computing power for. DPA attacks are dangerous because they circumvent the hardware and.
GitHub is where people build software. R1 and R2 are the. DEvis DEvis is a powerful integrated solution for the analysis of differential expression data.
Differential-power-analysis Star Here are 10 public repositories matching this topic. The option VectorScale allows one to fix the. Very limited reverse engineering Harder to confuse Cons.
There are many side-channel attacks which employ power analysis for discovering secret keys. More than 65 million people use GitHub to discover fork and contribute to over 200 million projects. Abstract This tutorial will introduce you to the basics of the DPA Differential Power Analysis a technique that exploits the dependency of the processed data on the power trace of the device to extract some secret information that would not be otherwise available.
This tutorial will introduce you to the basics of the DPA Differential Power Analysisa technique that. The second part of the tutorial DPA - measurement with an oscilloscope covers the practical part of the exercise - the. The attac er computes a-sample di eren tial trace 1 Dkb y nding the di erence bet w een a v erage of traces for whic h D C.
Statistics and cryptography for the attack. The attac er computes a-sample di eren tial trace 1 Dkb y nding the di erence bet w een a v erage of traces for whic h D C. Th us D jisthe a v erage o er C 1m of the e ect due to the v alue represen ted b.
Differential Power Analysis for Beginners Abstract. The method does not attack the cipher but the physical implementation of the cryptographic system. ADuCM36x Getting Started Tutorial Noise analysis.
DPA attacks measure power levels at different parts of the chip and apply statistical analysis to overcome countermeasures such as added noise that are applied to obscure individual bits. Understanding Differential Power Analysis Dpa Youtube 2 Electronics Free Full Text The Design Of Compact Sm4 Encryption And Decryption Circuits That Are Resistant To Bypass Attack Html. All 10 C 2.
This tutorial provides information on statistics and cryptography for the attack itself programming skills and experience in instrumentation to build up an automatic measurement system and electronical skills to improve the results. Over the past year and a half we have been working with the smart card vendor community to. The first part of the tutorial Differential Power AnalysisKey Recovery is aimed at explaining the creation of the power hypothesis and the use of algebraic systems.
Differential power analysis tutorial Written By bybel Tuesday March 29 2022 Add Comment Edit. We have 724 tags so the default is binspline. The second part of the tutorial.
Performing a Differential Power Analysis DPA attack requires knowledge in several fields. Different kinds of Differential Power Analysis DPA - first order Single-Exponent. Differential Power Analysis DPA Use statistical properties of traces to recover key Pros.
Difference of means traditional DPA Correlation power analysis CPA 19. Differential equations Exponential models. Differential Power Analysis DPA is a powerful method for breaking the cryptographic system.
Differential power analysis tutorial Written By dwainwolinski62590 Wednesday April 27 2022 Add Comment Edit. This paper describes various methods Hamming weight Hamming distance Switching distance and Signed distance and approaches like Simple Power Analysis SPA. Linear-regression side-channel dpa cryptography-tools differential.
Differential Power Analysis DPA is a powerful method for breaking the cryptographic system. K s is one and the a v erage of traces for whic h is zero. A differential power analysis DPA attack is an exploit based on an analysis of the correlation between the electricity usage of a chip in a smart card and the encryption key it contains.
Differential power analysis tutorial. Differential power analysis tutorial Written By darroncelentano87808 Friday June 3 2022 Add Comment Edit.
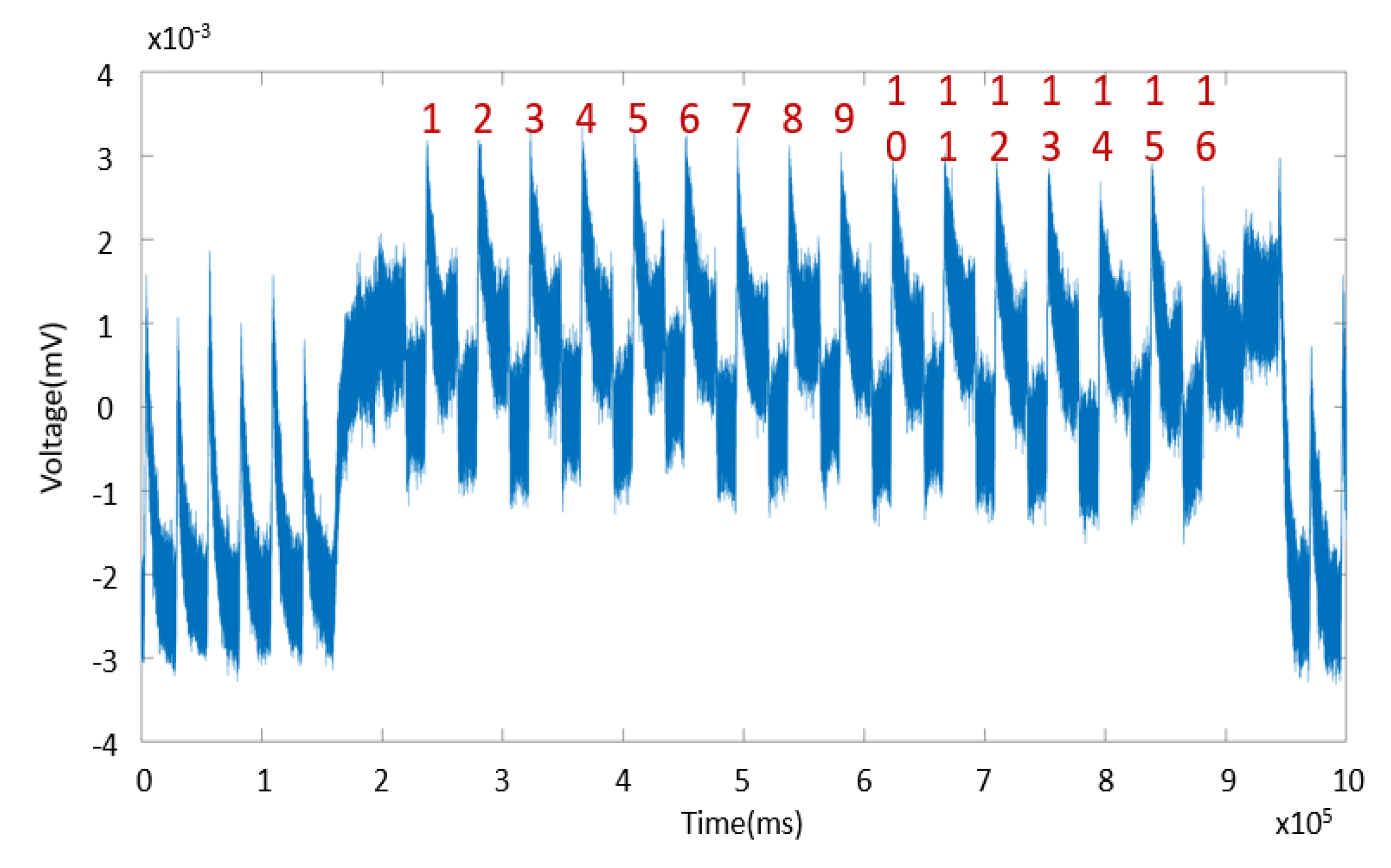
Cryptography Free Full Text Power Side Channel Attack Analysis A Review Of 20 Years Of Study For The Layman Html

Side Channel Attacks By Differential Power Analysis Nathaniel Graff Youtube

Breaking Aes With Chipwhisperer Piece Of Scake Side Channel Analysis 100 Youtube

Cryptography Free Full Text Power Side Channel Attack Analysis A Review Of 20 Years Of Study For The Layman Html
Power Analysis For Twin Studies

Breaking Aes With Chipwhisperer Piece Of Scake Side Channel Analysis 100 Youtube

0 comments
Post a Comment